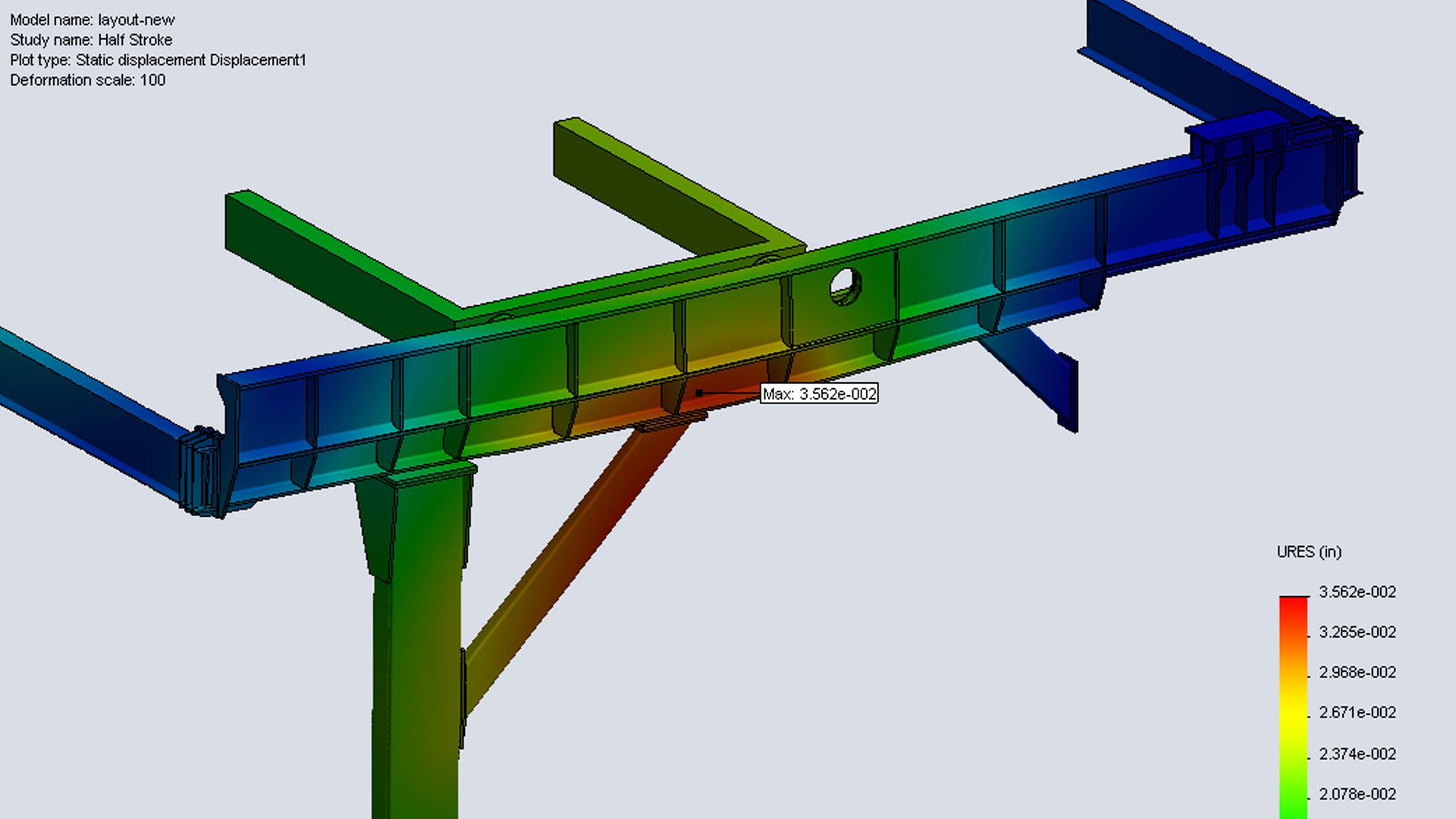
How Has COVID Changed Manufacturing?

We are moving past COVID -19, but the impact on manufacturing has been significant. The ability of manufacturers to adapt to new technology and cloud-based solutions has been helpful. in addition, they need to be able to automate processes quickly to adapt to change.
Automation:
There has never been a better time to build better products faster. Automation allows manufacturers to improve collaboration, increase yields, and find problems sooner by automating the manufacturing process.
How do manufacturers identify solutions for automation and how do they know when to invest in the technology? That is a great question. Investing in automation is costly, so identifying the highest priority processes is key to driving innovation forward on the manufacturing floor. Where does the manufacturing process bottleneck? What is the cost of failing at that point in the process? How will technology eliminate the bottleneck in the future?
The pandemic actualized these pain points for many manufacturers all over the world. Entire production lines went down for weeks with workers being isolated by COVID-19. To stay competitive and fill orders, manufacturers turned to investing in automation to improve the stability of the assembly line.
Management in manufacturing development a new mindset focused on flexibility. They looked at the worst-case scenarios of what would happen if, and when it happens how do we overcome that obstacle? Automation has propelled manufacturing forward at lightning speed and through automation, manufacturing will now be more agile to adversity both on the line and with software solutions.
Cloud-Base Software Solutions:
Manufacturing in the United States has radically changed since Henry Ford invented the assembly line. Innovations in technology have gone from using human capital to computer automation. One area where manufacturing had to improve to stay operational during the Covid Pandemic was with cloud-based software.
Today there are several ways that manufacturers can utilize cloud-based software:
- Infrastructure as a Service (IaaS) Allows manufacturers to access virtual computing resources. This includes technology like cloud servers and cloud storage. Examples include Apex which is offered by Dell Technologies. and Azure offered by Microsoft.
- Platform as a Service (PaaS) delivers resources that allows you to run apps, not just software development. Examples include Azure which is a cloud based application solution offered by Microsoft. PaaS supports the complete web application lifecycle. From building, testing, deploying, managing, to updating.
With cloud computing or cloud-based infrastructure, new software can be rolled out with little to no time wasted.
“Manufacturing has been notoriously slow to adopt cloud technologies - in part due to outdated concerns about the comparative security of cloud storage vs on-prem.” -Forbes
Connecting management to the manufacturing floor was key during the Covid Pandemic. Cloud-based software helped to ensure visibility through every step of the process while maintaining distance to try and curb the spread of Covid. The last thing manufacturers wanted to happen is to have to shut down a line. Technology helped to move that pain to a long-term solution with flexible cloud-based software that can integrate into legacy systems.
Supply Chain:
In 2022, supply chain challenges continue to impact manufacturing. A shortage of truck drivers and rising consumer demand continue to drive change in the manufacturing world. Raw material and parts from overseas also impact the ability of American manufacturers to maintain optimal manufacturing processes.
“The economic impact of COVID-19 revealed flaws in global manufacturing and supply chain thinking that were already ripe for change.” Glenn Richey, Harbert Eminent Scholar and Chair of the college’s Department of Supply Chain Management
Through automation, manufacturers can anticipate supply chain issues, but overcoming them is another matter entirely. Controlling costs with unstable sourcing has thrown many companies into a tailspin. Manufacturing companies have become increasingly international and often global. While international sourcing is on the rise, the pandemic has shown that access to the sources for your supply can be drastically affected by international interruptions.
“As a consequence of all this, manufacturers worldwide are going to be under greater political and competitive pressures to increase their domestic production, grow employment in their home countries, reduce or even eliminate their dependence on sources that are perceived as risky, and rethink their use of lean manufacturing strategies that involve minimizing the amount of inventory held in their global supply chains.” HBR.org
As a result, risk management in the supply chain has come into focus over the last few years and will continue to impact manufacturing going forward. Mitigating risks and developing strategic plans to prevent additional bottlenecks are essential to modern manufacturing. Automation and software are helping companies to identify and find possible solutions faster.
Conclusion:
Today, the need for automation and technology to prevent and mitigate problems with software is an essential part of the business. The ability to react quickly to change can mean the difference between surviving adversity and shutting your doors completely. Seifert Technologies specializes in helping manufacturers with innovative software solutions, and automation to ensure our clients with process improvements for the 21st century and beyond. If we have learned anything over the past few years, nothing is guaranteed, and flexibility is essential.
Contact us today to get started.